More pipes, grep, and strings
Welcome back to my 5th iteration of this blog series. In this series we’re growing our cybersecurity knowledge starting from the very basics using the overthewire.org challenges as a guide. First, I’d like to thank everyone for their feedback based on the last post! I’ll do my best to implement it and as always, more feedback is always welcome. Now let’s start!
The password for this level is in the “data.txt” file. Let’s take a look at the file:

That’ll be hard to sort through one by one; not to mention all the alarms we would set off if we attempted to figure out the password by simply running through the list. Let’s take a look at the hint again: “the only line of text that occurs only once”. We can use the uniq command to find that:

Hmm…the output is still the same. Let’s try sorting first then uniq:

We can see that sort reorganizes the contents into lines that repeat. Let’s add uniq to the commands:

So uniq here printed every line once: it only printed the lines the first time appear and doesn’t print them again. But uniq compares lines to each other, so without sort uniq thinks every next line is unique since it only compares to the line before.
uniq still printed too many lines, we only want the one that doesn’t appear anywhere else in the file as a whole, not print every unique line. We have to options here -c and -u. -c will tell us how many times a line appears but still print all unique lines:

We can also just print that one line directly with uniq -u:

We’re working with the “data.txt” file again but this time we’re looking for a the “human readable” text. If we were comparing files we could have used find like before. Fortunately, we were given a way to locate the text in the file: it’s preceded by several “=” signs. So let’s take look at the file:

Sure enough, that’s not human readable. Let’s try using grep like before:

Not the response we expected. We used this same syntax for grep before and we know it works. In this case, cat is the issue: it doesn’t play well with binary files: let’s try strings:
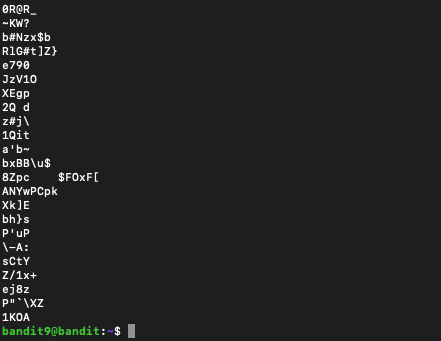
strings automatically finds the “human readable” text and only prints that. Now we can pipe this to grep and find our password:

This time we explored a new command to read files: strings. Functionally, it’s the same as cat except that it only prints what’s “meaningful to people”. Hiding sensitive information in files is common practice for data exfiltration. It’s most commonly used with pictures and is called steganography. Knowing how to examine different files for sensitive content is a necessary tool for keeping data secure. We can use these methods to set up data loss prevention software and tools to prevent the exfiltration and unauthorized removal of data.






